Intro
Every opportunity comes with risks, and DeFi is no exception. For every way you can make money in DeFi, it seems there are at least two ways you can lose it. Although these risks can’t be avoided entirely, with careful risk management and sensible judgement, you can at least decrease your chances of getting totally rekt.
So what are some of the most common ways people lose money in DeFi? What are the different types of hacks and exploits? And most importantly, how can you minimise your chances of being negatively affected by hacks in the future? You’ll find answers to these questions in this article.
And one more thing before we start. This article is a collaboration between Finematics and rekt.news.

Rekt News is an anonymous platform for whistleblowers and DeFi detectives to present their findings to the community. They analyse all the major hacks and exploits, and provide creative commentary on all things crypto and DeFi, with an aim to educate and entertain their readers. Their site rekt.news contains their own articles as well as an AI-generated news aggregator that gives coverage of all the most important recent events within crypto and DeFi in particular.
So, back to the topic of the article, how can I get rekt in DeFi?
We wouldn’t have time to cover every single type of exploit, and of course, many types remain unknown, but there are a few techniques that occur regularly, and we’ll now look at a few examples.
The Rug Pull
To “rug pull” has become a commonly used term across all of DeFi, and is now used to refer to many types of hacks and exploits, but it actually refers to a specific technique of suddenly removing the majority of liquidity from a liquidity pool.
The sudden loss of liquidity can create a death spiral for the token, as token holders try to sell as fast as possible in order to save their profits.
To rug pull is usually the final move from a malicious team and is a common form of “exit scam”, where the protocol deletes all traces of Social Media as they try to escape with the funds.
As this type of attack is technically very simple, it is often the chosen technique for quick cash grabs by low effort projects, however, this does not mean the profits are low, and there have been several major rug pulls where users have lost multiple millions.
One such example would be the case of Meerkat Finance, who after just one day of operation, were rugged for 13 million busd and about 73,000 BNB, totalling around $31m at that time.

If a large liquidity pool is used within a project, then the project team should not have the ability to retrieve these assets. If they do, then you are placing your trust in the project team.
Initially, Meerkat Finance did not have this ability, however, shortly before the attack, the Meerkat Finance Deployer “upgraded” 2 of their own vaults, giving themselves the ultimate backdoor into the vaults.
How can we avoid getting rug pulled?
Check how the liquidity is locked, is there a timelock, is there a multisig?
Do your research into the project, find out who is backing it and what is the purpose of the project.
Is the team known? If they are, what can you find out about them? Proving identity online is becoming increasingly difficult, and scammers are turning to unusual methods to build the trust of others, as was the case with DeTrade Fund, who some suspected to have used deepfake technology to create a video of a fake CEO. This story was covered by rekt.news (Deepfake – A Scam so Surreal).
On the other hand, if you can’t find any information on who is behind the project, remember that an anonymous team isn’t necessarily a bad thing, as the founder of Bitcoin remains anonymous to this day.
Economic exploit / Flash Loan
There was a period of time when it seemed every week brought a new DeFi hack, and the words “flash loan” were never far from the scene.
The association of flash loans with “hacks and exploits” led many in the community to believe that their impact was solely negative.
However, it’s worth remembering that these transactions were already possible for whales with large accounts, and that flash loans in themselves are not a malicious tool – they simply give access to large amounts of funding on a very short time frame. This funding can then be used to take advantage of loopholes in code, or to manipulate pricing and profit from arbitrage.
Flash loans are uncollateralised, unsecured loans that must be paid back before the blockchain transaction ends; if not repaid the smart contract reverses the transaction, so that it’s like the loan never happened in the first place.
Because the smart contract for the loan must be fulfilled in the same transaction that it is lent out, the borrower has to use other smart contracts to perform instant trades with the loaned funds before the transaction ends.
If you want to learn more about flash loans check out this article here.
Most flash loan attacks involve the manipulation of the token price using a large amount of capital.
One example of a major flash loan attack would be Harvest Finance, who lost $33.8 million to an attacker in October of 2020.
fUSDT fell 13.7% and $FARM fell 67% over two hours as the hacker took out a $50m USDT flash loan, then used the Curve Finance Y pool to swap funds and stretch stable coin prices out of proportion.
The following actions took place in a 7 minute time period.
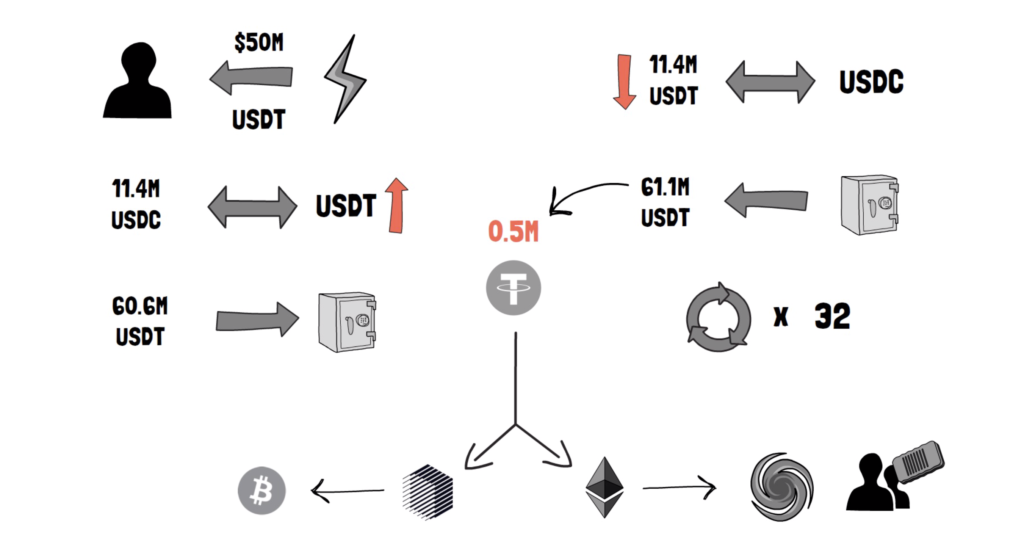
- Take a $50m USDT flash loan
- Swap 11.4m USDC to USDT -> causing USDT price to go up
- Deposit 60.6m USDT into Vault
- Exchange 11.4m USDT to USDC -> USDT price goes down
- Withdraw 61.1m USDT from Vault -> resulting in 0.5m USDT profit
- Rinse and repeat 32 times. (without any prior testing)
- Convert to renBTC and exit to BTC and ETH via Tornado Cash (a service that allows for making anonymous transactions on Ethereum, therefore covering the attacker’s tracks)
The attacker was able to withdraw more USDT at step 4 because of the changed USDT price. As the price of USDT was lower during the time of the withdrawal, their shares represent more USDT from the Vault pool.
Approximately 4 cycles can fit into a 10m gas limit, and although the profit on each cycle was less than 1%, ~$500k per repetition adds up quickly.
Flash loans are often used to manipulate prices, which allows for arbitrage where it would otherwise not be possible. To avoid flash loan price manipulation attacks, protocols should look to use reliable decentralised oracles.
Flash loans can also be used for other attack methods such as re-entrancy, front-running, or Arbitrage.
Arbitrage
Arbitrage refers to taking advantage of price differences between different markets in order to generate a profit. These types of opportunities are especially common in immature markets such as DeFi and crypto. Arbitrage opportunities tend to decrease as liquidity increases and the market becomes more efficient.
If a pool is manipulated (with flash loans for example) to allow room for arbitrage, then this may also be considered an exploit, as liquidity providers can end up losing their funds, as was the case with Saddle Finance.
During their launch in January this year, at least three major arbs took over 7.9 BTC ($275,735) from the early liquidity providers within 6 minutes, despite their claim to “have solved the problem of slippage”
4.01 BTC $139,961 Jan-19-2021 04:06:54 PM +UTC
0.79 BTC $27,573 Jan-19-2021 04:08:46 PM +UTC
3.11 BTC $108,548 Jan-19-2021 04:12:37 PM +UTC
Although this was only arbitrage, the users still lost out, as Saddle Finance was unable to protect them from the arbitrageurs, who were simply buying and selling, within the limitations of the code.
This brings us to one of the common questions regarding losing funds in DeFi
“Was it a hack, or was it an exploit?”
DeFi is still such a new concept, and the entire industry is a live experiment, testing new ideas as we build a new financial system. This means that loopholes are often found in live code, and when these loopholes can be used to withdraw funds without forcibly manipulating anything, then perhaps it’s best called “an exploit”.
However, this labelling could be applied to all hacks, as they can only operate with the code that has been written. Whether we call them a hack or an exploit, the end result is the same. If loopholes exist, then eventually someone will take advantage of them, and there is little we can do to stop this.
Even security audits do not guarantee safety.
Audits
rekt.news also ranks each hack and exploit on the rekt.news leaderboard, which shows not only how much was stolen from the protocol in dollar value at that time, but also who audited the protocol before the hack.
If we look at the rekt leaderboard, we can see that the majority of hacked (or exploited) protocols actually had a security audit completed prior to the attack. This proves that an audit is not a guarantee of safety, and audit firms can also fail.
The leaderboard shows who audited the specific piece of code that was exploited.
According to the leaderboard, the most notorious security companies are currently; Peckshield with 3 failed audits, Certik with 2, and Quantstamp also with 2.
Many of the most recent rekt.news articles covered audited protocols, showing that in the end, there is very little difference between an audited and unaudited protocol.
Users often make the mistake of believing that one security audit can cover an entire protocol forever, however, all DeFi protocols are full of moving parts, and even if a protocol is audited very thoroughly, a single small update can render the audit useless.
Summary
So what do you think about hacks in DeFi? Have you ever been affected by any of them?
Also, don’t forget to check out rekt.news for more content like this.
If you enjoyed reading this article you can also check out Finematics on Youtube and Twitter.